Infamous ransomware families, malicious programs that encrypt victims’ files preventing legitimate access until a ransom is paid, had a drastic impact in the past years. We proposed a novel approach, ShieldFS, that is able to detect malicious behaviors and revert the effects of ransomware attacks, which means no files lost for the end users!
By Andrea Continella
PhD Student @ Politecnico di Milano, soon joining the SecLab @ University of California, Santa Barbara as a Postdoc researcher.
In the last year, ransomware has been one the most dangerous Internet threat. Preventive and reactive security measures can only partially mitigate the damage caused by modern ransomware attacks. The remarkable amount of illicit profit and the cybercriminals’ increasing interest in ransomware schemes demonstrate that current defense solutions are failing, and a large number of users are actually paying the ransoms. In fact, pure-detection approaches (e.g., based on analysis sandboxes or pipelines) are not sufficient, because, when luck allows a sample to be isolated and analyzed, it is already too late for several users! In May 2017, the famous WannaCry family propagated leveraging an old vulnerability in Windows systems and infected more than 200,000 computers across 150 countries, with total damages ranging from hundreds of millions to billions of dollars.
We believe that a forward-looking solution is to equip modern operating systems with generic, practical self-healing capabilities against this serious threat.

Proposed Approach. We proposed ShieldFS, a drop-in driver that makes the Windows native filesystem immune to ransomware attacks. ShieldFS creates detection models that distinguish ransomware from benign processes at runtime on the base of the filesystem activity and it applies the detection approach in a real-time, self-healing virtual filesystem that shadows the write operations and reverts the effects of ransomware attacks, safeguarding the integrity of users’ data. Thus, if a file is modified by one or more malicious processes, the filesystem presents the original, mirrored copy to the user space applications. This shadowing mechanism is dynamically activated and deactivated depending on the outcome of the aforementioned detection logic. For this, ShieldFS monitors the filesystem’s internals to update a set of adaptive models that profile the system activity over time. This detection is based on a study of the filesystem activity of over 2,245 applications, and takes into account the entropy of write operations, frequency of read, write, and folder-listing operations, fraction of files renamed, and the file-type usage statistics. Additionally, ShieldFS monitors the memory pages of each “potentially malicious” process, searching for typical artifacts that are indicators of the use of block cipher encryption schemes.
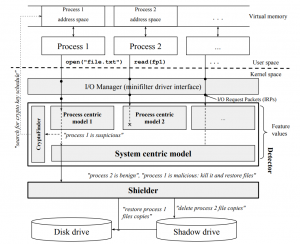
Whenever one or more processes violate our detection component, their operations are deemed malicious and the side effects on the filesystem are transparently rolled back.

Experimental Results Summary. We evaluated ShieldFS in real-world working conditions on real, personal machines, against samples from state of the art ransomware families (including WannaCry, CryptoLocker, TeslaCrypt, Locky). ShieldFS was able to detect the malicious activity at runtime and transparently recover all the original files, with negligible false positives.
 Andrea Continella on Twitter: @_conand
Andrea Continella on Twitter: @_conand
