The increasing popularity of the smartphones attracted lots “bad actors” that wants to spread malicious software into the ecosystem for profit. To avoid being detected and maximize profit, malware uses evasive techniques. We propose an approach to combat evasive malware.
By Chengyu Zheng
PhD student @Politecnico di Milano
How to avoid being detected
With over 500 million devices and an estimated 84% market share, Android-based devices are the main target for cyber-criminals. In addition to the alarming amount of malware families and samples, evasive techniques used by malwares are becoming more and more sophisticated. With the high amount of new applications being released every month, “app store” maintainer are struggling to find a reliable solutions to analyze apps in order to recognize and isolate malicious ones.
Techniques used to analyze apps can be divided in two category, namely static and dynamic analysis. Static analysis allow us to obtain sound information on entire portions of an application. However, in practice, code obfuscation technique is used to render static analysis tools so imprecise to become unusable. Dynamic analysis on the other hand are not affected by obfuscation, but it comes at the expenses of the code coverage.
Most of the modern malware nowadays uses obfuscation to avoid being analyzed statically, but in addition to that, some of malware also uses evasive techniques to avoid being analyzed dynamically. To achieve that, malware uses heuristics that detect artifacts present in the environment used by the analysis. This is extremely effective since most of the dynamic analysis tools are based on emulators.
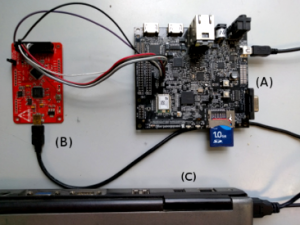
The hardware based-approach
We proposed a hardware based sandbox for analyzing android malwares. This approach is able to defeat the heuristics used by malware to evade analysis. Our system takes an apk and generates the syscall trace of the application. To achieve that we place a hardware breakpoint in the syscall handler. For every syscall triggered by the apk we parse the memory and reconstruct the full arguments.
We conducted an experiment, where we used 2 families of known malware samples that uses evasive techniques against emulators, run it both in an instrumented emulator and our hardware-sandbox, and we compared the number of the syscalls made by the application.
Using the emulator we were able to intercept ~30 syscalls while using our approach we were able to intercept ~3000 syscalls, meaning that we successfully avoid the malware from evading our analysis.
In conclusion, we showed what malware try to use to void detection and how hardware-based sandboxes can be used to analyze evasive malware.
For further information you can read the article published at the IEEE Communications and Network Security (CNS, 2016)

