Domain specific languages for robotics are hardly considered as an attack vector—however, we found that they expose sensitive primitives that enable vulnerabilities and malware. In an upcoming BlackHat talk and ASIA CCS paper, we will present the security-relevant impact of such code primitives, and we will introduce a code analyzer we built to automatically detect “insecure” uses of such code primitives.
By Marcello Pogliani
Research Collaborator at the NECSTLab, working on Systems Security
This post is a “preview” of a research work that will be presented at Black Hat USA 2020 on August 5th, 2020.
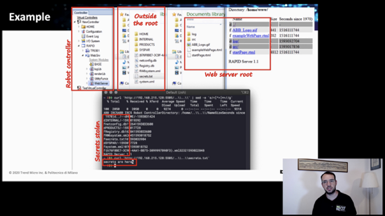
The history of this work goes back to 2017, when we published a paper showing what happens when and if sophisticated adversaries compromise an industrial robot. While working on that research, we learnt that robots can be programmed through proprietary domain-specific languages (such as RAPID by ABB or KRL by KUKA). Digging deeper, we witnessed that complex programs built in such languages can go way above and beyond simply moving the robot: we found among the ABB RobotApps a web server entirely written in RAPID. Moreover, we found that the web server was vulnerable to a path traversal—allowing a network attacker to download arbitrary files from the robot controller, including sensitive configuration files.
Back to now, this observation motivated us to dig deeper on this topic, asking ourselves what is the security impact of the languages’ “sensitive” features, and what vulnerabilities are present in programs written in such languages.
Surveying 8 among the most widely known languages, we observed that they expose security-sensitive features such as the ability of reading from and writing to the robot controller’s file system, the ability of performing some form of dynamic code loading, and networking capabilities. We observed that these features enable taint-style vulnerabilities (and, thus, that programs written for such languages should be analyzed for vulnerabilities!) and that they potentially allow malware to be developed in such languages (think about functionalities such as file dropper and network scanners). The paper presents more details about the functions that act as sources and sinks to enable different “classes” of vulnerabilities: arbitrary network movement, path traversal, arbitrary function execution.
Naturally, we also wanted to know if there are actually real vulnerable programs, besides the aforementioned web server, and how many. To this extent, we built a prototype static source-code analyzer for programs written in domain-specific languages for robots (to date, it supports KRL and RAPID). This prototype performs taint analysis to find unsanitized paths between (configurable) sources and sinks in the program—allowing to find instances of vulnerabilities.
As a dataset, we downloaded various programs from public sources (e.g., Github). As robot programs are highly sensitive and proprietary, we found mostly educational or demonstrator programs. However, we found about 100 among RAPID and KRL files that use at least a function to gather data from the network. Out of these files, we found that the most widespread issue is arbitrary network-controlled movement (13 projects, totalling 34 files); then, we found 1 project with a path traversal and 2 projects leading to arbitrary function execution.
Curious about the details of our research? Head over to the project page, read the preprint of the article that will be published at ASIA CCS 2020 or look at our talk at Black Hat USA 2020 (which will be aired on August 5th, 2020).
Note: this research is a collaborative effort between myself, Federico Maggi (Senior Researcher at Trend Micro), Davide Quarta (Postdoctoral Researcher at EURECOM), Marco Balduzzi (Senior Researcher at Trend Micro) and Stefano Zanero (Associate Professor at the NECSTLab). We also thank Martino Vittone (Master’s Student at the NECSTLab) and Mario Polino (Postdoctoral Researcher at the NECSTLab) for their contributions to a preliminary study that led to this research.

